MITF
The MITF (Malware Investigation Task Force) began its anti-malware activities in May 2007. It deploys honeypots to the IIJ network in a manner similar to general users, and monitors attacks from the Internet as well as the status of malware activity. It also formulates countermeasures based on information gathered by obtaining and analyzing attack records and malware specimens.
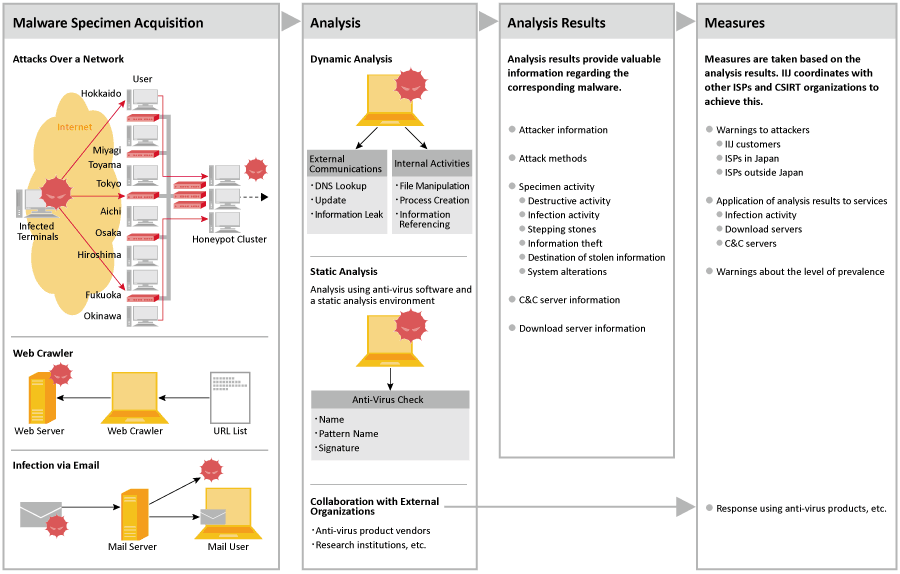
MITF Honeypots
Honeypots are a type of system used to assess attacker trends. The MITF uses them to observe malware activity and obtain specimens. Malware is a generic name for malicious programs such as computer viruses, worms, bots, scareware, and crimeware.
The MITF uses honeypots that emulate the behavior of functions such as Windows File Sharing (SMB) and RPC to monitor the activity of malware that attempts to exploit vulnerabilities. Because honeypots are simply connected to the Internet and do not communicate actively, attempts to communicate with them are likely to be either attacks or precursors to attacks.
In other words, when a user involuntarily attempts to communicate with a honeypot, the computer they are using is suspected to have been infected with malware. Users may be contacted when this kind of communications is detected.
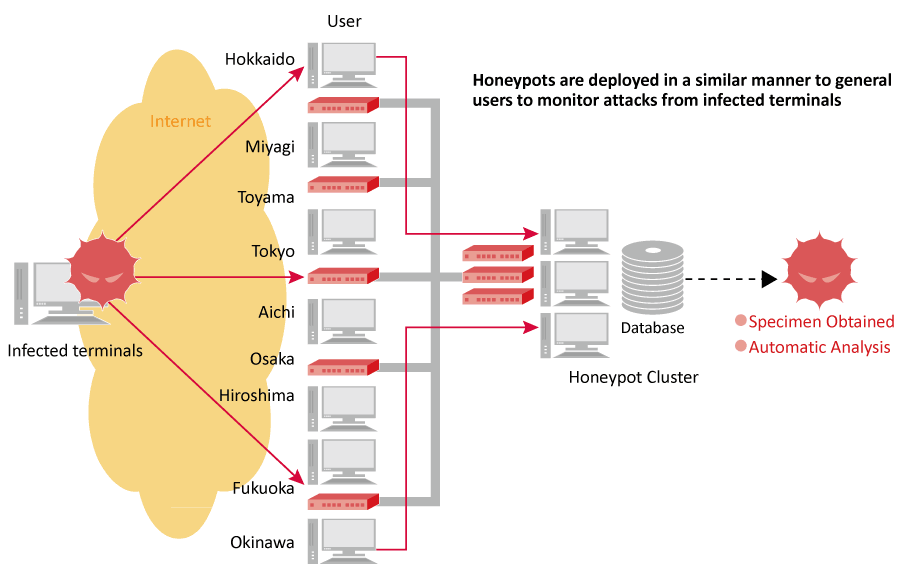
Web Crawlers
This type of malware infects users that visit malicious websites built using tools such as Exploitkit, as seen in cases such as Gumblar and ru:8080 that have drawn attention in recent years.
Many of these websites were originally harmless sites that were altered using methods such as SQL injection attacks or unauthorized access exploiting login credentials stolen via malware.
Web crawlers are designed to monitor whether any user websites on the IIJ network are malicious or are set to redirect to malicious websites. When such a website is discovered the user may be notified or the site may be taken offline temporarily.
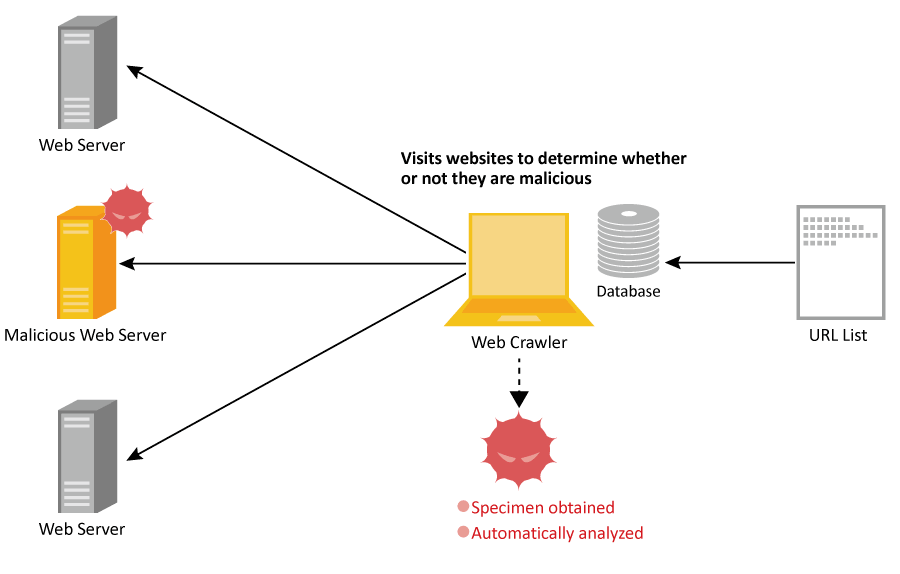
Dynamic Analysis and Static Analysis
The MITF uses dynamic analysis and static analysis to examine the characteristics of each malware specimen obtained via these methods.
Dynamic analysis is a technique for identifying a malware’s type and behavior by observing what happens when malware is executed in an analysis environment. This dynamic analysis environment is constructed in isolation from the Internet, making it possible to examine malware safely.
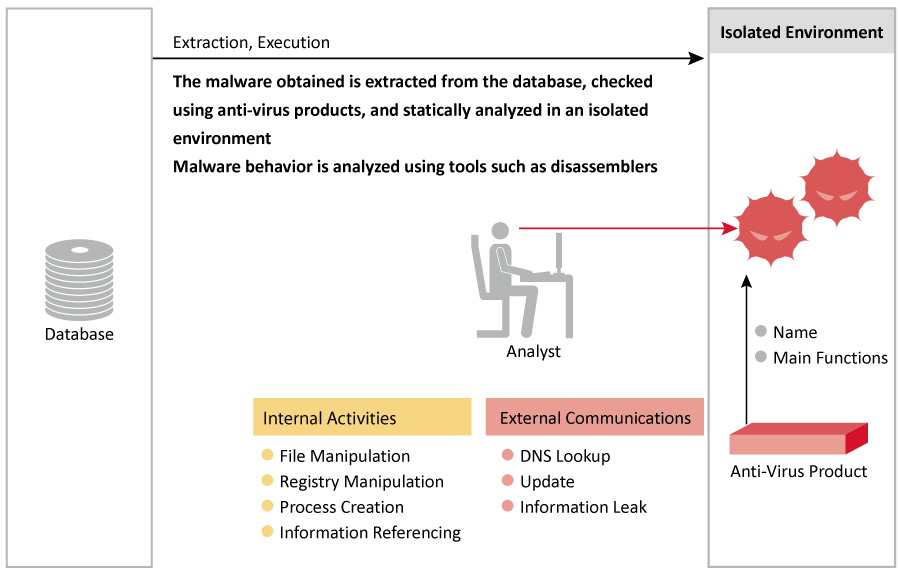
Static analysis is a technique for examining the architecture and analyzing the behavior of malware obtained without executing it. It involves the use of anti-virus software or tools such as disassemblers or debuggers for analyzing executable files.
Malware that does not operate in a dynamic analysis environment or that we would like to investigate further is examined manually using analysis tools.
Using these forms of analysis we can identify the files created or deleted and the registry details changed on computers infected with malware, as well as the servers that distribute malware and the C&C servers that control bots. We then issue warnings based on this information and implement measures for the services in operation.
External Blacklists
There are sites on the Internet that release lists of IP addresses that have caused harm to users, such as IP addresses used in attacks, IP addresses used in attempts to send spam, and websites thought to be infected with malware.
The hosts registered in lists such as these may belong to the individuals conducting attacks or to victims of hijacking that have been infected with malware and hacked.
IIJ monitors these lists on a regular basis, and when IP addresses on the IIJ network are registered, users are contacted as necessary to request that action be taken.
