New TINYSHELL based Linux malware related to UNC5325
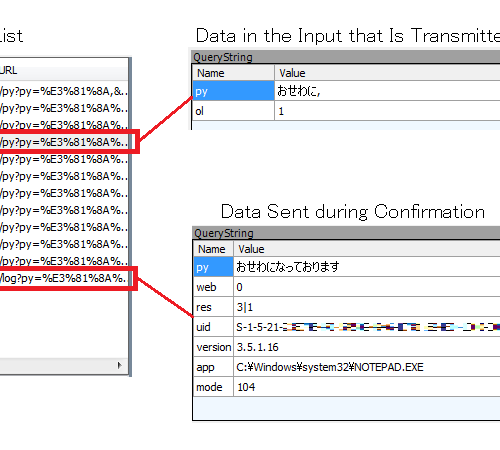
In June 2025, we discovered the dropper of new TINYSHELL based Linux malware. Because this malware had code overlapping with PITHOOK, reported to be used by UNC5325, we are confident that this malware is related to attack campaign of UNC5325. UNC5325 is suspected to be China-nexus espionage actor, whose reported to be exploiting vulnerability of Ivanti Connect Secure (CVE-2024-21893) in...
READ MORE New TINYSHELL based Linux malware related to UNC5325